Hashing
Intro
In the digital world, encryption and authentication are critical. I realize that hashing is a huge topic, so here is a fast overview.
A hashing algorithm is a mathematical algorithm that converts input data to an output string (hashing key) of a fixed length. Hashing key is unique (depending on the data), irreversible (data could not be generated back from the hash string), and identical for the same data if the same algorithm is used. Hashing string also has a constant length (for the same algorithm) no matter the data size is.
e.g. if you tried to hash 'a' (1 Byt) or an image (10 MB) using the same algorithm, the output will be a hash string at the same length in both cases but they will be different of course
applications of hashing
Hashing has many applications, such as copying files, checking if a file is edited or not, encrypting, authenticating, and checking if what you sent is received as one piece (fully received in the correct order). Hashing is also used to distribute data into sections hash tables (sorting).
Let's have copying files as an example. When you copy any file the system will generate a hashing key for both copies and compare them to ensure that the copy is identical to the origin.
Popular hashing algorithms
There are a lot of hashing algorithms such as MD5, SHA, RSA, Scrypt, and Ethash. I will explain two of them a fast algorithm and a secured one. [1]
MD5
MD5 is hashing algorithm that generates a key of 32 characters (letters and numbers). This means that each key size is 16 bits (each character is 4 bits) [2]. It is usually used to check if two files are identical or not. The main advantage of it is it is fast but it is not highly secured. However, it is way more efficient than MD4.
The MD5 hashing algorithm uses a complex mathematical formula to create a hash. It converts data into blocks of specific sizes and manipulates that data a number of times. While this is happening, the algorithm adds a unique value to the calculation and converts the result into a small signature or hash. [3]
SHA
SHA is one of the most secured hashing algorithms in the world. it is designed by the United States National Security Agency and used for bitcoin and the International Criminal Tribunal of the Rwandan genocide [4]. The hashing key size is 64 bytes which is the maximum useful size [2]. The most popular SHA versions are SHA-256 and SHA-512

HS, and RS
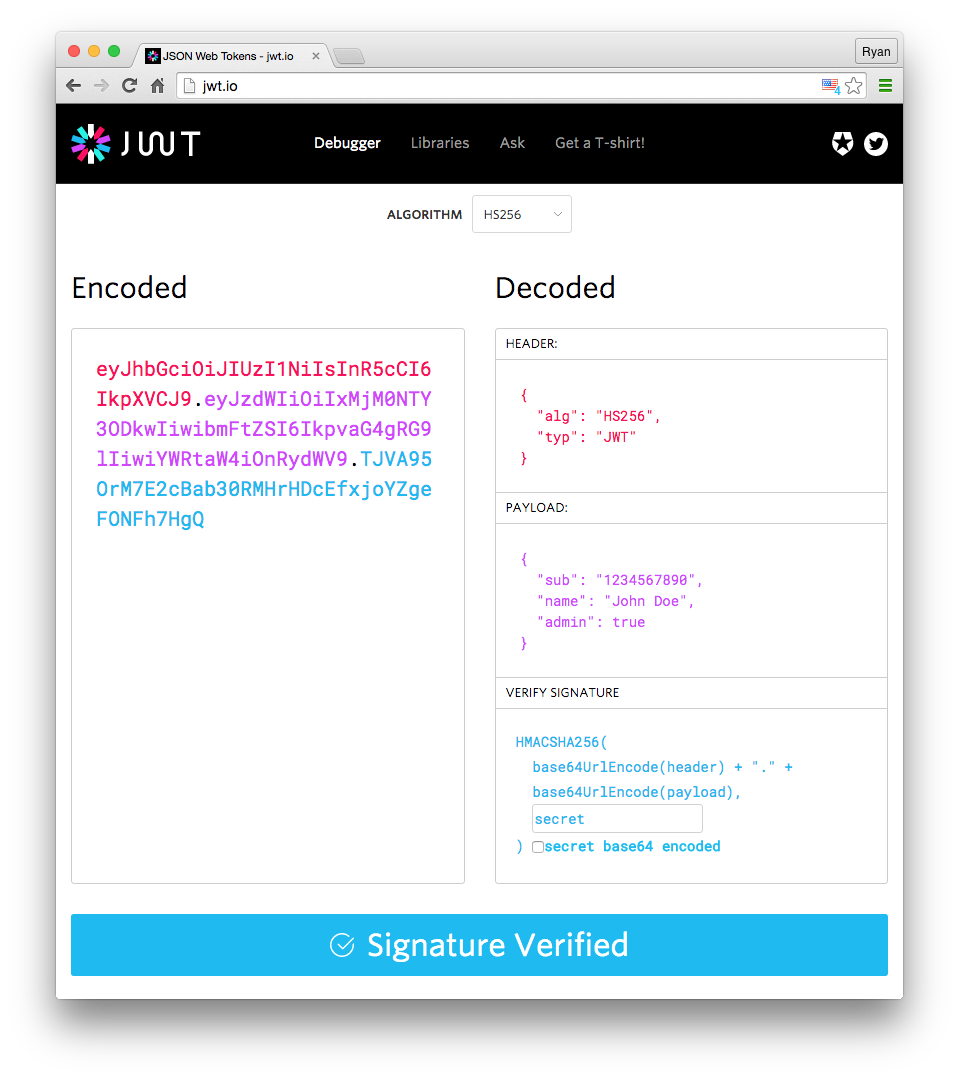
They are hashing algorithms used with JSON Web Token (JWT). Basically, JWT is used for authentication and then for authorization. JWT has three main parts: header, payload (body), and signature, all of them are hashed JSON data separated by a dot.
HS256 is a symmetric keyed hashing algorithm that uses one secret key. Symmetric means two parties share the secret key. The key is used for both generating the signature and validating it. [5]
RS256 is an asymmetric algorithm that uses a public/private key pair. The identity provider has a private key to generate the signature. The receiver of the JWT uses a public key to validate the JWT signature. The public key used to verify and the private key used to sign the token are linked since they are generated as a pair. [5]